CompTIA Security+ Exam Pro iOS and Android App
Level Up Your Cybersecurity Expertise!
Introducing CompTIA Security+ Exam Pro — your go-to app for mastering the CompTIA Security+ (SY0-701) certification. Whether you're breaking into cybersecurity or refining your skills, this app is designed to elevate your professional knowledge.
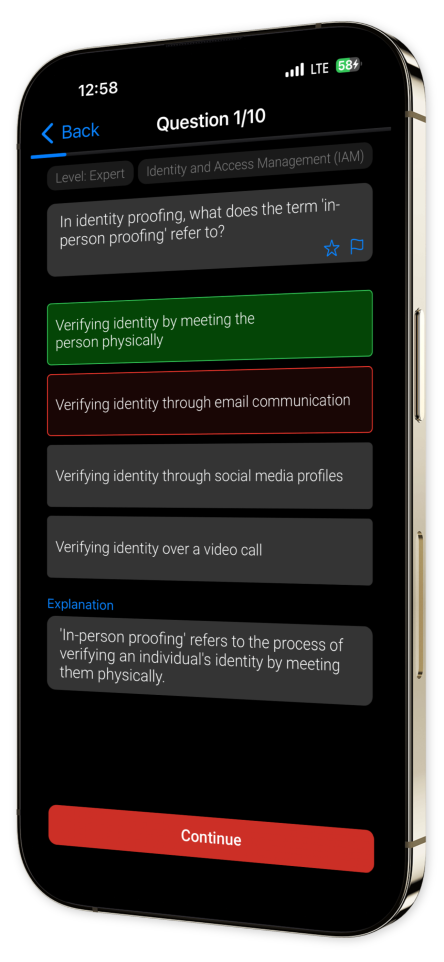
Tackle a full range of practice questions covering key areas like threat detection, security protocols, risk management, and incident response. Each question is paired with detailed explanations so you can dive deeper into the `why` behind every concept.
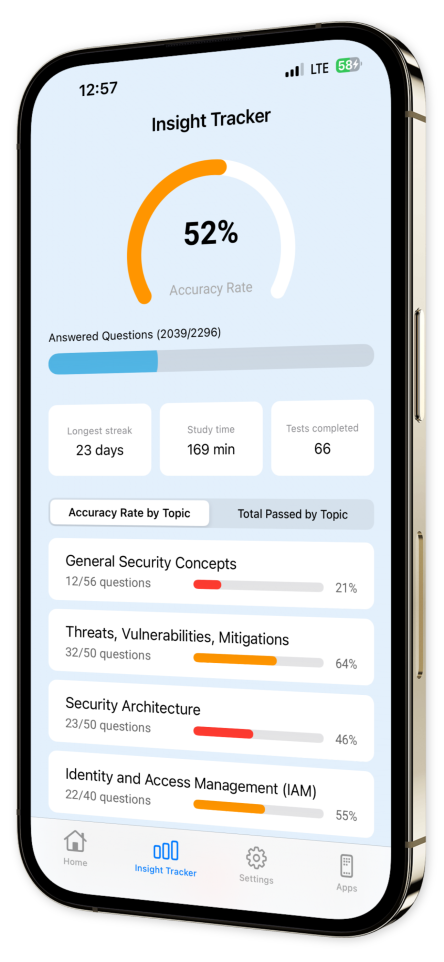
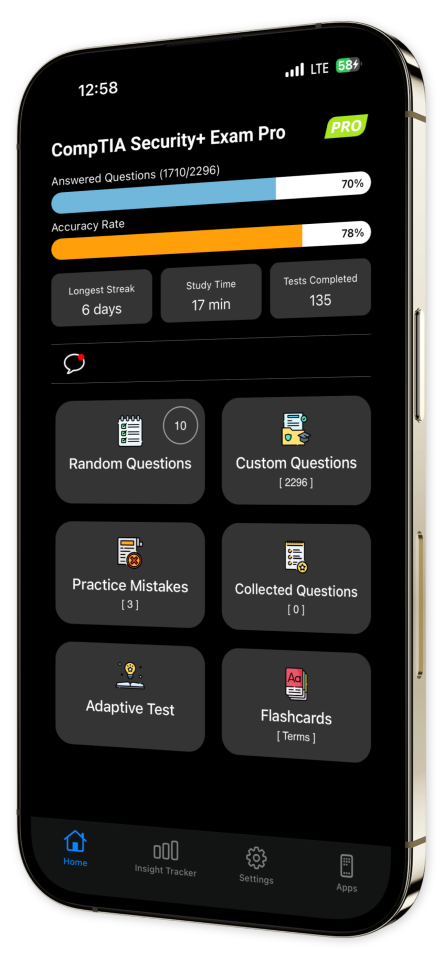
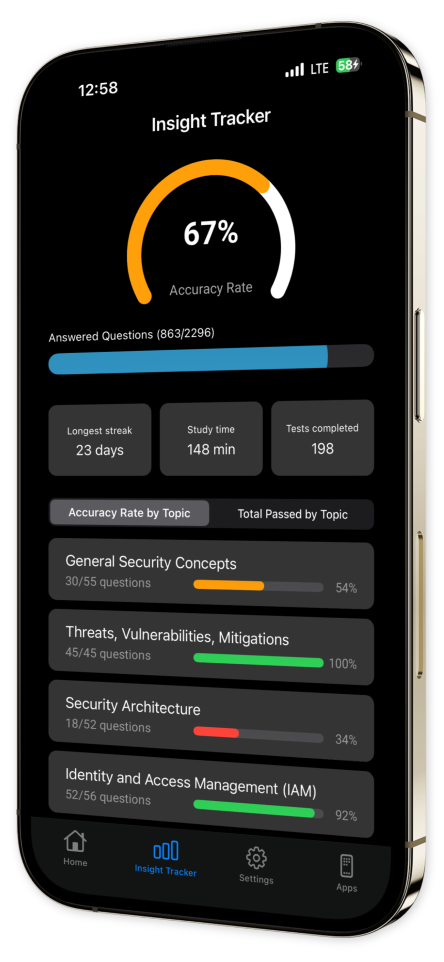
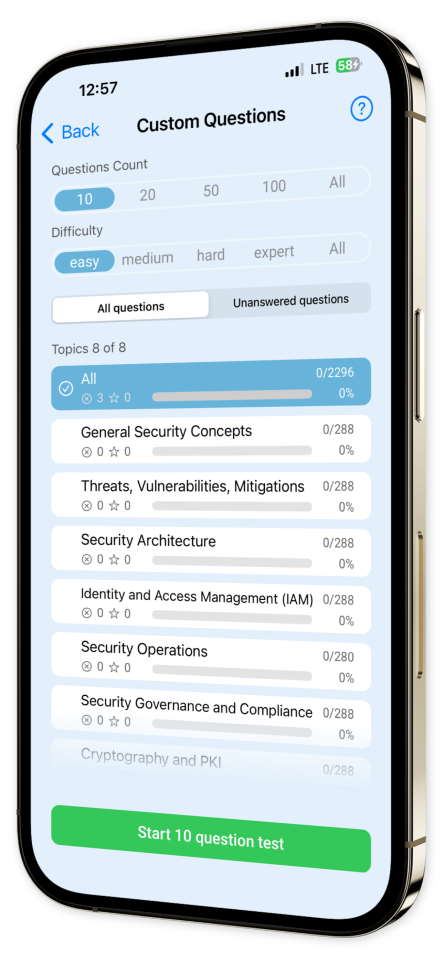
Take control of your study path with custom quizzes focused on your specific needs. Track your progress and build a personal library of tough questions to ensure you’re fully prepared for the exam.
Thousands of professionals have already advanced their cybersecurity skills with CompTIA Security+ Exam Pro. Get certified, stay ahead, and elevate your cybersecurity expertise. Download now and take the next step in your career!
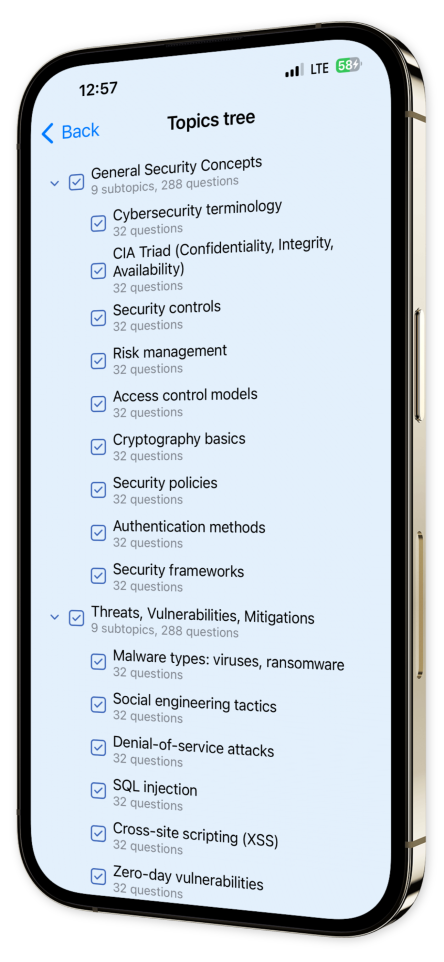
Content Overview
Explore a variety of topics covered in the app.
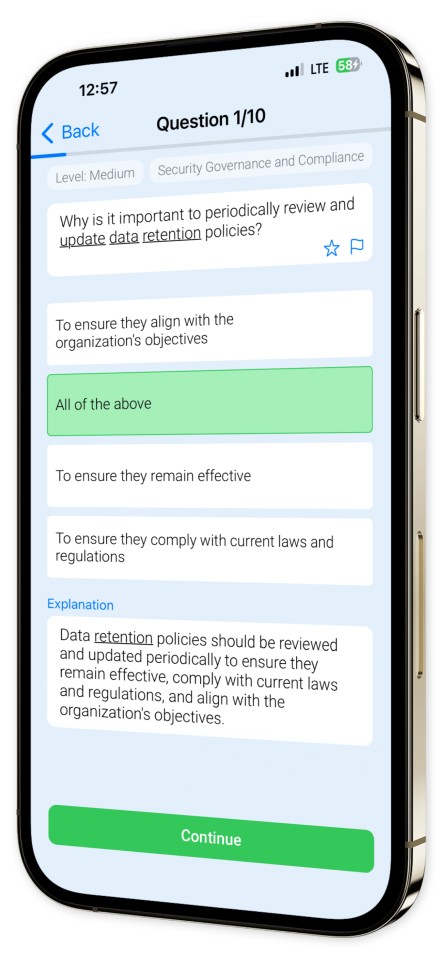
Example questions
Let's look at some sample questions
What is the primary disadvantage of a packet-filtering firewall?
High costComplex configurationLack of context awarenessInability to filter traffic
The primary disadvantage of a packet-filtering firewall is its lack of context awareness. It examines each packet individually without considering its context.
What is 'sandboxing' in the context of virtual environments?
A method for isolating applicationsA technique for encrypting dataA strategy for managing VM sprawlA type of hypervisor
Sandboxing is a security mechanism used to run an application in a restricted environment, or 'sandbox'. This isolation prevents the application from accessing system resources or data beyond its confines, thus limiting potential damage if the application is compromised.
What is the purpose of network segmentation in secure network design?
To increase network speedTo reduce the number of firewalls neededTo limit the spread of threats within a networkTo make it easier to monitor network traffic
The purpose of network segmentation in secure network design is to limit the spread of threats within a network. While it can also make it easier to monitor network traffic, this is not its primary purpose. It does not increase network speed or reduce the number of firewalls needed.
Which access control model is best suited for high-security environments?
DAC modelMAC modelRBAC modelABAC model
The Mandatory Access Control (MAC) model is best suited for high-security environments. It is often used in military or government settings where information classification and confidentiality are of utmost importance.
What is the first phase of the incident response lifecycle?
Containment, eradication, and recoveryPreparationPost-incident activityIdentification
The first phase of the incident response lifecycle is preparation. This phase involves creating an incident response plan and setting up the necessary tools and resources to handle incidents.
What is the first step in creating a disaster recovery plan?
Identifying potential disastersCreating a disaster recovery teamConducting a business impact analysisPurchasing disaster recovery software
The first step in creating a disaster recovery plan is conducting a business impact analysis. This involves identifying critical business functions and systems, determining the impact of a disruption to these functions and systems, and establishing acceptable recovery timeframes.
What is the main purpose of the NIST Cybersecurity Framework?
To provide a standard for software developmentTo provide a guide for IT governanceTo provide a guide for managing and reducing cybersecurity riskTo provide a standard for project management
The main purpose of the NIST Cybersecurity Framework is to provide a guide for managing and reducing cybersecurity risk. It is not focused on software development, IT governance, or project management.
What is the purpose of a chain of custody in digital forensics?
To document the evidence collection processTo ensure that evidence is collected in a timely mannerTo ensure that evidence is collected by authorized personnelTo document the analysis of the evidence
The purpose of a chain of custody in digital forensics is to document the evidence collection process. It helps to establish the integrity of the evidence by tracking its handling and storage from the time it is collected until the time it is presented in court.
Why is it important to document an incident?
To assign blameFor insurance purposesTo improve future response effortsTo make employees feel guilty
Documenting an incident is important for improving future response efforts. It allows organizations to learn from their mistakes and prevent similar incidents from occurring in the future.
What type of intrusion detection system uses statistical models to detect anomalies?
Signature-based IDSAnomaly-based IDSBehavior-based IDSNone of the above
Anomaly-based intrusion detection systems use statistical models to detect anomalies in network traffic patterns.